
As hybrid clouds become more common, the complexity and related risks increase significantly.
Using just a lift and shift approach is not enough to exploit the advantages of the hybrid cloud. It takes some homework before to understand and design a cloud migration. At the beginning, it should be clarified why the new technologies are being used, what requirements result from them and who is building up or providing the necessary skills.
An extended infrastructure using on premises and cloud applications requires proper mapping and needs to be controlled to ensure business continuity combined with accurate and reliable IT systems.
Companies aim to find the best way to combine on premises applications, public cloud services, private cloud services and services from multi cloud structures. It is often not easy to adapt and change quickly to remain agile in the digital business transformation since business critical and security sensitive applications are mostly to remain on premises. The same applies to services which are regulated under law and not all services can be obtained from the cloud.
In order to adapt the business needs and choose wisely which cloud model fits best, an overall hybrid cloud operating model is required. IT departments face the risk to diverge infrastructure and applications and missing the holistic approach. For example, the infrastructure sponsors favor Microsoft’s Azure and the application sponsors favor AWS because of their artificial intelligence or machine learning capabilities.
Shadow IT Risks
An organization may end up with a multi cloud strategy by accident, via a shadow IT. That is technology adopted by business units independently of the IT department, which may subsequently be ‘reined in’ for oversight by the CIO.
Often in the past, single subsidiaries or regions choose services from the cloud on their own initiatives to transform their business more quickly. This resulted in a shadow IT, diverged from the corporate IT strategy, with a mess of different and unaligned SaaS products.
The extent of shadow IT revealed by McAfee’s 2019 Cloud Adoption and Risk Report is startling: 1,400 IT professionals in 11 countries were asked to estimate the total number of cloud services in use in their organization and came up with an average of 31. The actual average figure was 1,935:
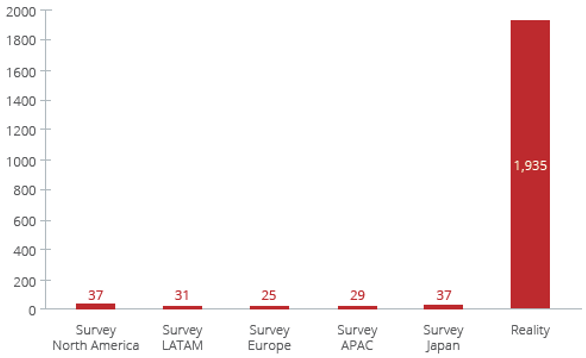
Estimated versus actual levels of cloud service usage. Source: McAfee
At this point, companies recognize the need for a sourcing strategy. It forces you to understand why you want to go to the cloud.
No one should move a well-established on premises service to the cloud just because the cloud seems cool and modern.
There is no value if the services remain the same. The service from the cloud should contain new and transformative results which bring benefits to the customer.
Security Risks
Choosing a public cloud means less control over data security. Risks are mainly about data transfer, data leaks and data privacy. You depend on your vendor in which country and under which regulations your data is managed. All the data is travelling on the internet between the company’s network and the cloud service provider’s network. Secured channels must be ensured.
The risk analysis depends on the workloads, contractual controls with the public cloud service provider, architectural controls in the software and application environments and technical controls regarding the IT infrastructure. Just migrating to the cloud does not mean that companies become more vulnerable. It depends on the right architecture and how the cloud security tools are integrated.
The data which customers upload to the cloud is with their own responsibility. Cloud service providers take care about the cloud but not what is inside the cloud because customers configure the applications, they define access control and data sharing rules.
Companies should pay attention to the following questions before going to the public cloud:
- Can the public cloud service provider meet the companies information security needs?
- Does the contract with the cloud service provider and the terms and conditions ensure the companies and security standards?
- Does the cloud service provider guarantee international governance standards such as the ISO 27000 series of security and privacy standards, especially ISO 27001 and ISO 27017 for IT security, ISO 27017 for cloud services security and ISO 27018 for cloud services related to data protection such as privacy and GDPR compliance?
- Does the cloud service provider follow architecture standards such as ISO 17789 for the cloud computing reference architecture, ISO 18384 for SOA reference architecture, ISO 24760 for ID management architecture and ISO 29101 for privacy architecture framework?
- In what extent is the cloud service provider liable for data leaks?
- How does the cloud service provider handle information security for its own staff and data centers?
- How well is the software configured where the data go to the cloud, especially when workloads are running on both private and public clouds?
- What cloud workload protection solution does the vendor offer? What are the further protections apart from endpoint protection platforms?
- Where do we have lack of skills to understand the new environment and architecture of the hybrid cloud?
- Which API controls exist to monitor and regulate the data flow between on premises servers and the public cloud?
- What kind of Hardware Security Modules (HSM) are in place to ensure trustworthiness and integrity of data in the hybrid cloud?
- What Trusted Execution Environments (TEE) does the cloud service provider offer to ensure a secure and trusted runtime environment for applications? This relates both to cyberattacks and Identity Access Management (IAM) questions.
The biggest risk is during the migration to the cloud, however, as functions and services will change over the time, the risk analysis is a repetitive task and the international standards provide minimum audit cycle recommendations.
A high risk threat for cloud workloads is related to misconfigurations. Incorrect set up of Identity Access Management (IAM) systems and weak data transfer protocols increase cloud workload vulnerability. As the code of cloud applications change, the permission changes too and this can lead to more misconfiguration. Outside attackers focus on accessing data through phishing emails by targeting cloud workloads as they are exposed though the internet. Companies need to set up mechanism or check with vendor to detect malicious code in their productive hybrid cloud environment. Cloud workload protection is critical and the new threat model against cloud workloads is new and different from protecting on premises environments.
Companies should ensure that the security tools offered are compatible with their operating systems and other applications used from the same vendor. For example, if a company is using Microsoft’s Azure Cloud solution, they offer security tools such as Azure Active Directory, Identity Access Management (IAM) tools, encryption and network isolation services. If the customer does not run the latest Windows operating system, they cannot use the full system management capabilities offered.
Nowadays, cloud service providers respond to the risks by having such high security standards and measurers so that customers would spend much more costs and time to develop those skills and standards in house.
So it can also be seen as a benefit if the in house measures have a lower standard than what the vendor provides.


